Ever run into a problem where you have a .PDF file that’s password protected, only you’ve forgotten the password?
I went on the hunt for the best PDF password recovery utilities for the Mac, and the resounding pull of the tide was to Recover PDF Password by Eltima Software.
The version reviewed here is Version 3.0, Build 3.0.40.
With a PDF file, it turns out there can be two passwords.  The owner password in Adobe Acrobat called the change permission password, which is used to inhibit changing the document, restrict printing, copying, and other related features.  The user password merely allows opening the file.  Recovery PDF Password can not only recover them both, but remove them as well, rending a neutered document; it can also remove a digital signature.
PDF passwords are not simple obfuscation, that would be easily reversible and insecure. Â Instead, cracking the encryption involves walking the key space, a task that Recover PDF Password is capable of doing, even when the password contains Unicode characters, using multiple cores to accomplish the feat.
Given that the key space is actually quite enormous, and that users often pick weak passwords, Recover PDF Password can leverage this fact if you know a little bit about your password already. This is what makes Recover PDF Password rather clever —intelligently narrowing down the key space to only try passwords that are likely.
To start with, there’s a Dictionary attack, which will not only try a common list of words, numbers, or your own common password collection, but it will also perform a number of common heuristic checks against permutations that humans commonly do, such as altering upper and lowercase, reversing, replicating characters, dropping characters, adding characters, etc. This gets more bang for your buck out of common password lists.Â
Here’s 62 thousand common passwords to get you started.
While trying a known dictionary is very quick, it doesn’t work against unique, inventive passwords. Â To do that Recover PDF Password can also be made to use a brute-force attack. Â Again, it has the ability to narrow down the key space to something much more manageable. Â It does so by allowing you to specify a minimum and maximum password length, you can provide a wildcard template of what you suspect the password is, or you can conduct a completely exhaustive search.
It’s also possible to limit the characters to uniquely or a combination of lowercase, uppercase, digits, symbols, white space, or additional characters of your choosing.
Recover PDF Password provides a coarse estimate of how long the process will take, the elapsed time so far, and the passwords found. As walking the key space to discover a password can be fairly CPU intensive, this is often a task left to the background or when you’re not using your machine. This is why Eltima built a pause and resume feature in, so that you can put the process on hold, use the full power of your machine, and then resume without having to start all over again. Also, if it’s already discovered the password to a file, it doesn’t have to recompute it (unless you want it to), as it remembers the prior password for a file for you.
The user interface is fairly straight forward, and the online help adequately addresses any subtle questions that might surface. Not only can it recover the password, but it can be used to provide information about the .PDF file as well.
There are some limitations to be aware of, as of this version the software can only recover the password for Adobe .PDFs for version 9 using 256-bit encryption. Â Additionally, it’s possible with some really exotic passwords to find a match, but not be able to physically enter it. (See Note #1.) It also will not support removing a Digital Certificate (a Digital ID) due to International Copyright Law. Â (See Note #2.) Â These conditions are rare, but worth knowing about.
It’s also important that user expectations be set up front about the timeliness of the brute-force task. Encryption isn’t supposed to be easy to crack, and it’s supposed to be prohibitively expensive to brute-force.
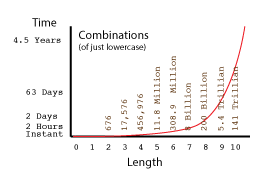
Recover PDF Password will usually get a 6 character password in a fairly short period of time. However, a 9 character password results in an estimation of “more than a day.” The problem with that is, according to How Secure Is My Password, a somewhat trivial password of that length can take several days, and a complex choice of characters can bump that up over 80 years. Â Another site showing tables of Password Recovery Speeds computes that even just mixed upper and lower case characters can take from a month to several millennia. Just single case alphabetics can run in months to years.
This explains why strong passwords are usually at least 12 characters long, contain multiple character classes, and abide by rules to increase password complexity. In a nutshell, if the password you’re trying to recover is too long, or too complex, Recover PDF Password will theoretically get it, but your patience will have long run thin, your hardware’s mean time to failure will come upon you, or you’ll expire yourself before it’s recovered. This is the value of a strong password.
The solution to that problem is clusters of machines working together on the problem, a tactic well-funded governments employ. Perhaps with cloud services and ever faster and more parallel machines becoming affordable, the reach of the average user will extend to cover slightly larger passwords. Eltima tells me they are looking at solutions that allow multi-machine cooperation on a network, and are giving consideration and thought to cloud servcies.
All this, of course, is thwarted by people using much longer and secure passwords today.
As such, being realistic about the matter, Recover PDF Password was able to recover short, simple passwords in a reasonable time, although the real-world passwords I use still require too much computational time to brute-force a recovery. But that’s where the software seems to be appropriately named, especially if you don’t think of it as a password cracker, but a recovery tool. See, most people have a general idea about what the password may be, but have forgotten the specifics of what variation that might have been used. Recover PDF Password’s dictionary and template modes allow for quick experimentation, and using that, I was able to recover a 9 character password because I had some idea about what it looked like and could cooperate in the reduction of the key space process. Recover PDF Password did the grunt work of trying all the possibilities.
In that respect, Recover PDF Password is quite a useful tool, but your mileage may vary based on password length, password strength, and your own recall.
I’ll also point out that when I tested this version with OS X Lion (v10.7.4), Recover PDF Password recommended I install Growl (which comes with the software). The only problem is that it is an older version than Growl available on the AppStore. Eltima has said they are going to reach out and become partners to restore the option with Lion; hopefully this happens before Mountain Lion his the App Store.
While Recover PDF Password is quite capable, there are a number of features I’d like to see in future versions, which I think would enhance the software immensely:
- Some additional dictionary heuristics, such as Leet substitutions — where ‘apple core’ is spelled as ‘@9913 (023’.
- The handling of a batch of PDFs at once — walk the key space once, check for all.
- Displaying passwords as found.
- Improved progress indicators: how many keys there are, how many it’s tried so far, the velocity of guesses per second.
- Provide realistic estimates, based on the average velocity, for the coverage of 50% and 100% of key space.
- Provide hints about how to reduce the runtime through stricter settings.
- Provide a Regular Expression-like syntax for far more complicated password templates.
- The ability to “nice” the guessing task — so that it always keeps humming away, but at a lower priority, rather then full-on or full-off.
- Allow a full quit of the application and to resume later where left off (adding more PDFs as well).
- Allow the user to enlist a cloud service — it pushes the hashes up and a whole slew machines beat on them.
- Where practical, build either a pre-computed hash table for quick look up, or grow an online comprehensive dictionary of new passwords to try.
- Provide realistic estimations before kicking off the job, thus allowing the user to tweak parameters and see the impact.
- Allow one to pause the job and refine the key space further — one might remember something more about the password and not want to start all over.
- Utilize the full power of multiple threads, multiple CPUs, the GPU, and if available other machines on the network — a generous license would do wonders for this software.
Quite a number of these suggestions resonated with Eltima Software, and I look forward to seeing more good things from them in the future.Â

